Betrayed by Your Dashboard: Discovering Malicious Campaigns via Web Analytics
Oleksii Starov1, Yuchen Zhou2,
Xiao Zhang2, Najmeh Miramirkhani1, and Nick Nikiforakis1
1Stony Brook University and 2Palo Alto Networks
WWW 2018
- Introduction
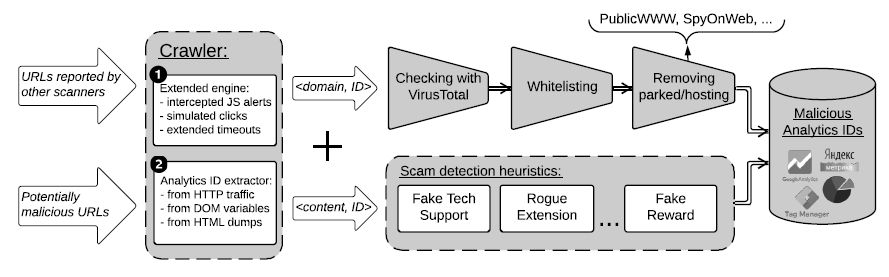
To better understand the demographics of their visitors and their paths through their websites, the vast majority of modern websites (including this one!) make use of third-party analytics platforms, such as, Google Analytics and ClickTale. Given that all the clients of a third-party analytics platform report to the same server, the tracking requests need to contain identifiers that allow the analytics server to differentiate between their clients.
In this work, we analyze the analytics identifiers utilized by eighteen different third-party analytics platforms and show that these identifiers enable the clustering of seemingly unrelated websites as part of a common third-party analytics account (i.e. websites whose analytics are managed by a single person or team). We focus our attention on malicious websites that also utilize third-party web analytics and show that threat analysts can utilize web analytics to both discover previously unknown malicious pages in a threat-agnostic fashion, as well as to cluster malicious websites into campaigns. We build a system for automatically identifying, isolating, and querying analytics identifiers from malicious pages and use it to discover an additional 11K live domains that use analytics associated with malicious pages. We show how our system can be used to improve the coverage of existing blacklists, discover previously unknown phishing campaigns, identify malicious binaries and Android apps, and even aid in attribution of malicious domains with protected WHOIS information.
This idea is conceived by the lead author, Oleksii Starov, when he was an intern at Palo Alto Networks. I am honored to be his mentor at that time. One of the more important outcome of this work (other than the publication itself) is that we eventually converted this work to be used in production and it helps improve our malicious website coverage. This is a prime example of industry-academia convergence and we are proud of what we have achieved here.
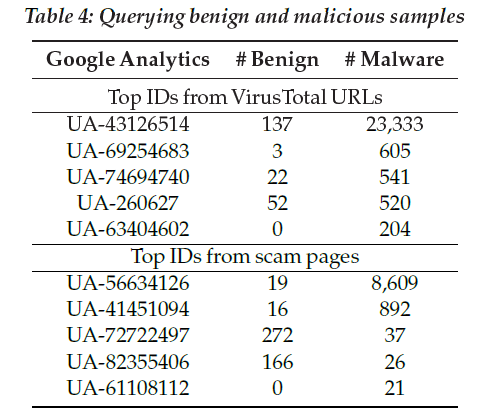
Some analytic IDs which indicates unequivocal maliciousness
- External link
Find more information on SUNY's security group page at here.
- Paper