Coin mining storm inside the browser
Note: This blog is a special version of official Palo Alto Networks Blog, authored by the same group of researchers. The link to this official version is at here.
Executive Summary
By analyzing PANDB logs, we found many of our customers were affected by the recent browser crypto-mining fever, with victims spanning all across the globe. We found over 35K URLs on more than 1000 domains leverages customer’s CPU time for crypto-mining for various reasons - many sites do this for extra monetization, while others are compromised by other attackers. Sites ranked as high as Alexa top 1000 were caught doing this to their customers. By analyzing embedded JavaScript, Whois and passiveDNS data, we are able to identify a couple major campaigns launched on mid September and early October, and attribute them to several major actors. The severity and popularity of the crypto-mining storm requires everybody to take immediate steps to protect themselves against this hideous act.
Cryptocurrency have taken the world by storm, from the biggest player ‘bitcoin’ to newcomers such as Monero and Ethereum. Cryptocurrency mining has thus become a hot industry, from powerful, dedicated mining hardware to exploiting graphics card’s parallel computing power. Recently, browser coin mining has taken off, for a lot of different reasons. Although the computing power (per instance) is much less than dedicated hardware, being able to exploit many users on various sites more than make up for it. There are already quite some media coverage on them, such as BBC, and malwarebytes. While we do not consider crypto-currency mining inside browsers malicious by itself, it is often time that such mining is going on without the end user’s consent or even knowledge that makes this practice shady and despicable.
Coinhive, one of the more popular browser-mining services out there offers site owners a piece of JavaScript for easy integration. Site owners exploit site visitor’s CPU time to mine XMRs (Moneros) for Coinhive, and Coinhive pays out 70% of mined value to site owners. A new player, crypto-loot emerged recently which offers similar services but pays out 88% of revenue.
1. Coinhive integration
On the official Coinhive homepage, we found detailed documentation on how to integrate the mining scripts onto any given website. Owners can use the easy version:
1 | var miner = new CoinHive.Anonymous('YOUR_SITE_KEY'); |
or more complicated version that gives control over how the end user’s CPU time should be used, e.g. how many threads, should the mining throttle.
1 | var miner = new CoinHive.User('YOUR_SITE_KEY', 'john-doe', { |
Higher thread number and/or lower throttle number will result in more CPU usage in client’s browser. With higher CPU occupation percentage, end users will likely experience sluggish behavior and poor experience on the websites.
2. Tracking coinhive integrations
We have been tracking the inclusion of coinhive mining script (coinhive.min.js) for a week, in our PANDB unknown feed. The amount of URLs leading to the download of such similar scripts is astounding. Since we started tracking, we have seen anywhere from 6K unique URLs to over 10K in one single day.
Overall, we have seen over 35,119 unique URLs associated with coinhive.min.js. Across these URLs, there are a total of 144 IPs and 1,025 hostnames. Based on our observation, the appearance of these scripts can be clearly divided into 4 categories - standalone, voluntary, and compromised.
Standalone hosting.
URLs like
1 | hxxp://gkiqfnjtwmj.bid/vhyk.php%3fr=1507428652%26v=3%26ilznfamx=1322781%26zptrfkmy=%26djpsicdr=%26adymouss=%26ruxhztvq=http://cricfree.cc/stream2watch/bt2.php%26s=1536%2c864%2c1.83%2c2810.88%2c1581.1200000000001 |
always hosts the following content:
1 | <html> |
It is worth noting that such URLs are always belong to a jibberish.bid domain, with a long trailing set of parameters. Of the 35,119 URLs we collected, 33,188, or 94.5% are of this category. In addition, there are 612 URLs leading to the same set of .bid domains, but with much shorter URLs, like hxxp://www.pudptxanhspld.bid/static/robots.txt, or even the domain itself: hxxp://www.pudptxanhspld.bid/. The fact that robots.txt is hosting the exact same content as any other longer URLs with seemingly random parameters leads us to speculate that the domain will serve the same coin-mining content to all visitors, ignoring the request parameters or paths. It is interesting to speculate, why did our customer visit such weird, long, random URLs in the first place? We give some of our speculations later in this blog.
After removing the .bid ones, we are left with 1,342 URLs, or 3.8% of the corpus. The remaining can be further categorized into the following three groups:
Crypto-mining related sites.
We found multiple URLs related to coin/crypto/mining keywords. Examples include
1 | http://www.coinnnnn.com/ |
Some of these are forums discussing crypto-mining, while others are introducing the concept. Regardless of the purpose of the websites, we did not find any evidence that such sites are asking user’s consent to mine XMRs.
Monetization.
This category include sites that obviously want to include coin-mining scripts to monetize. Examples of these include video/porn sites such as
1 | hxxp://xmoviesforyou.com |
While they do provide their normal service to the visitors, browsing these sites do not pop up any sort of warning of coin-mining behavior for the user. A script snippet embedded in such sites can be found here:
1 | ... |
What is more interesting is, that by searching in the whole URL corpus leading to coinhive.min.js download, we are able to find URLs such as
1 | hxxp://avditmiohvtq.bid/y.htm%3fr=1507583452%26v=3%26jfbakqer=2246476%26ipgznbkx=%26bwxtoxtb=%26oghaenqv=%26hsvxkzhp=http://www.xmoviesforyou.com/2017/10/momsincontrol-rebecca-rhiannon-ryder-pussy-is-international.html%26s=1280%2c800%2c2%2c2560%2c1600 |
which includes xmoviesforyou.com as part of the URL, almost like a referer parameter. We are able to verify that
1 | hxxp://www.xmoviesforyou.com/2017/10/momsincontrol-rebecca-rhiannon-ryder-pussy-is-international.html |
is indeed a valid URL leading to a subpage in the porn site. That site does include coinhive.min.js, but at the time of our re-confirmation, the inclusion is directly from https://coinhive.com/lib/coinhive.min.js, and the whole page does not include any references to a suspicious .bid domain/URL. We speculate that the porn website URL may have included an iframe leading to the .bid domain, which then triggers the download of coinhive.min.js. However, this mechanism may have been later abandoned in favor of direct inclusion.
Compromised/Injected integration
Another group of sites seem to have fallen victims of malicious script injection to their vulnerable servers. We found that hxxp://www.livetruemoney.com uses up 100% of user’s CPU time. Upon closer investigation, we found that this site is hosting multiple copies of coinhive.min.js, toward the top and bottom of the page. Similar situation happens in https://www.comptesofficiels.com/, where the snippet is injected outside of <body> tag (a common symptom for injected content), as follows:
1 | ... |
It is quite possible that crypto-mining has become a new injection vector in addition to traditional exploit kits redirections.
Finally, we have also seen some typo-squatting/phishing domains serving coinhive.min.js. Examples include analytics-google.net/track.php, and www-bank.ru.
3. Actor/Mining configuration analysis
According to our observation, coin mining integration scripts are rarely obfuscated, which means we can extract the anonymous ‘site key’ and their configurations easily. Per coinhive’s documentation, the ‘site key’ is a unique identifier to indicate which beneficiary will be paid, therefore, the attacker has no incentive to garble this field. Here are some interesting stats about the actors and their configurations.
Actor distribution
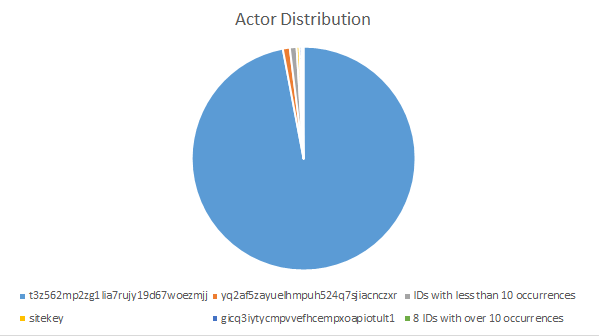
There is a clear winner at the top - ID t3z562mp2zg1lia7rujy19d67woezmjj claiming 35,742 over 36,842 of all the IDs we were able to retrieve. Surprisingly, querying a website source code search engine like publicWWW only returns 13 results (mostly .bid domains). The remote second and third scored 370 and 119 occurrences respectively, along with 8 other IDs topping 10. A long tail (146) of IDs only have 1 appearance in our dataset, and these are possibly category 2 or 3 in our integration scenarios described above - mining would benefit themselves rather than a campaign owner.
With no surprise, site key owner t3z562mp2zg1lia7rujy19d67woezmjj has all the .bid URLs pointing to this payee. In addition, there are URLs such as
1 | http://216.21.13.11/s%3fcid=5100604%26iuid=1619927385%26ts=1507160862%26ps=3429657830%26pw=2413%26 |
also using the same site key. Passive DNS analysis reveals that this IP actually was mapped to serve.popads.net, so it is interesting that this particular advertising network may have lead to crypto-mining behavior.
In this chart, a special case sitekey stands out. There are 151 sites using it, and it is a predefined variable in previous scripts (as opposed to hardcoded string) so without dynamic analysis we are not able to retrieve its real content. We took a look at a few samples and it seems that sites using the sitekey variable are more often than not serving mining script to benefit themselves.
We found only 6 out of the entire URL population making more than one call to coinhive.Anonymous function (which means they could possibly be compromised by two different adversaries/serving two different payees at the same time). Upon closer inspection, all the calls actually have the same site key, so in summary we did not find evidence of one site serving more than one beneficiary. We did, however, find out that one site, lottoipros.com, is attempting to obfuscate its site key by using simple unicode encoding:
1 | var _0x8cfd=["\x56\x63\x33\x38\x75\x32\x33\x35\x51\x67\x31\x55\x6E\x48\x78\x47\x43\x52\x6A\x59\x51\x4D\x58\x70\x6E\x4A\x73\x58\x77\x4B\x4C\x69","\x73\x74\x61\x72\x74"];var miner=new CoinHive.Anonymous(_0x8cfd[0],{threads:1,autoThreads:true,throttle:0.6,forceASMJS:false}) |
Clearly, the site owner/injector is aware of the risks of exposing its key and is trying to hide from public scrutiny. If this trend continues, it will become harder to use static analysis to detect crypto-mining sites.
Configuration distribution
The dominant Actor ID t3z562mp2zg1lia7rujy19d67woezmjj uses default configuration across all of observed URLs, so we exclude this actor from this analysis to prevent skew. We also exclude the 142 sites that use mineropts that go almost hands-in-hands with sites using sitekey as their site key.
This left us with 827 valid data points. Among these, most sites only uses 1 thread, by default; however, some sites use as many as 4 threads to maximize mining speed.
| Thread count | Number of sites |
|---|---|
| default (1) | 772 |
| 1 | 28 |
| 2 | 7 |
| 3 | 1 |
| 4 | 19 |
For throttling, other than the default setting which disables throttling, the most popular option is to set it at 0.5, so that the CPU would idle 50% of the time. It is suffice to say that most sites are not giving user’s CPU any break at all by disabling throttling.
| Throttle setting | Number of sites |
|---|---|
| default (0) | 772 |
| 0.5 | 28 |
| 0.2 | 25 |
| 0.7 | 19 |
| 0.9 | 10 |
| other values combined | 35 |
4. Hosting domain analysis
In this section, we show some hosting domain stats, including PassiveDNS and Whois data analysis.
TLD distribution
The TLD distribution for domains hosting coinhive.min.js is shown below. For brevity, we aggregated all TLDs having less than 20 entries into others category.
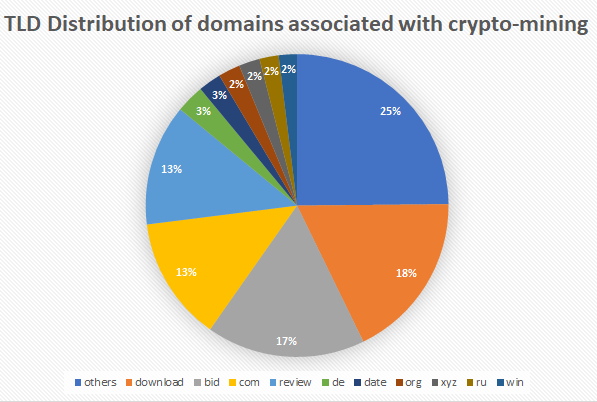
Clearly, the top suspects are .download and .bid domains, taking more than 35% of the total share of 1,025 domains. As expected, typically notorious TLDs like .xyz and .win is also listed.
Alexa rank distribution
We checked all associated domains against the current Alexa traffic ranking. The results are astonishing - there are 5 sites in top 2K, 29 sites in top 10K and 155 sites in top 1 million. We sample a few highest ranking sites and show it here:
| Site | Alexa Rank |
|---|---|
| uptobox.com* | 771 |
| 123movies.co* | 963 |
| cinecalidad.to | 1026 |
| watchfree.to* | 1892 |
| sugklonistiko.gr | 1910 |
*: At the time of the writing, we can no longer observe coinhive.min.js on their sites.
The highest ranked .bid domain, llxyyocfgfg.bid is ranked at 3380 at the time of this writing.
pDNS analysis
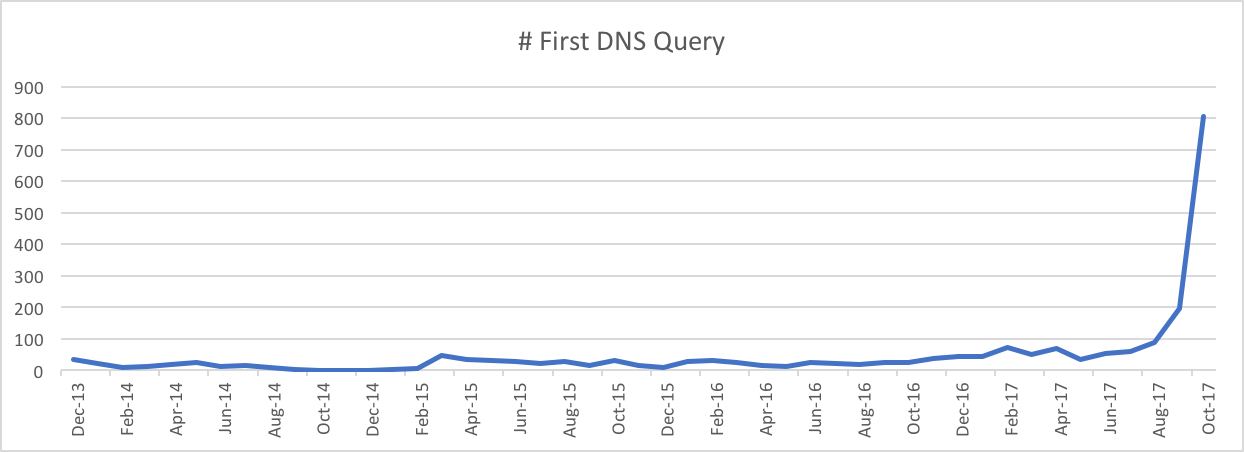
We looked up these domains in our passive DNS (pDNS) database. 794 domains were found with records among the 1026 domains in total. We found that the first DNS query to many domains dates back to the launch date of our pDNS in 2013, such as uptobox.com, torrent.cd, and tiexue.net. This means these websites have been active for a long time. Some of them are quite popular based on their Alexa ranking. So the potential impact of Coinhive can be high in both time and space. We also found that the first DNS query to 502 (63%) domains happened in October 2017. Based on the figure below, we can clearly see the emerging trend of these domains.
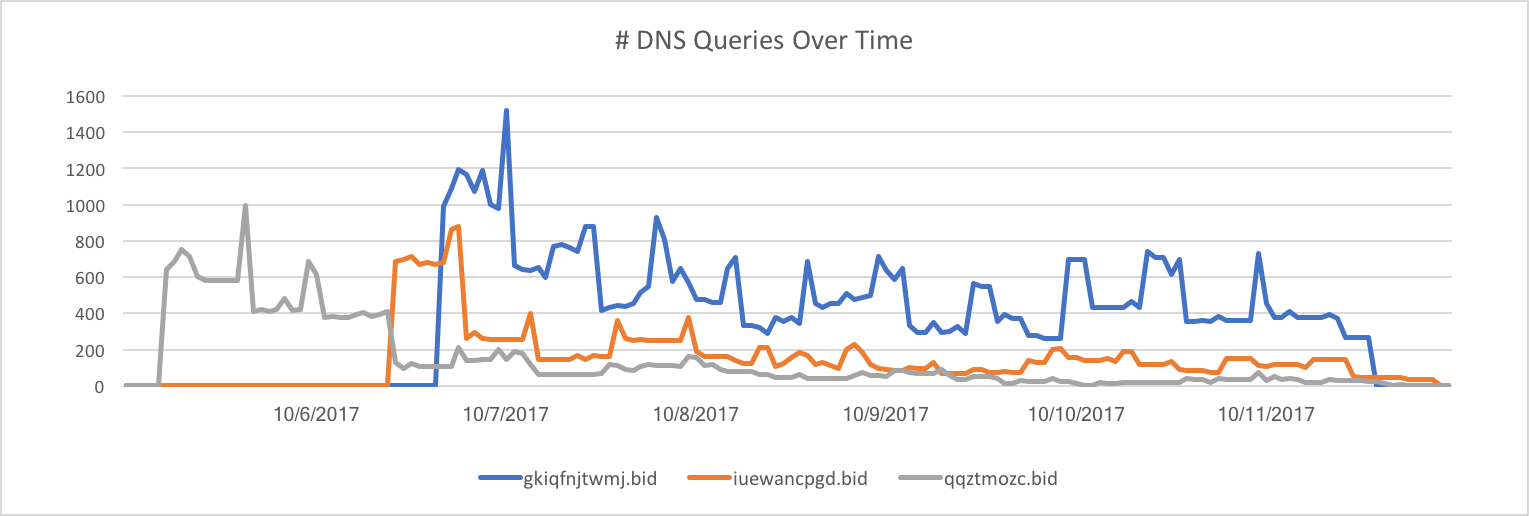
We further investigated the DNS query pattern of these domains. In particular, the following graph shows the number of DNS queries to these website per hour. Interestingly, we found that some domains exhibit very similar patterns. Although the start time and amount of traffic are slightly different, the overall pattern of traffic is very much similar in shape. This is another indicator that these domains potentially belong to the same campaign launched by the same owner.
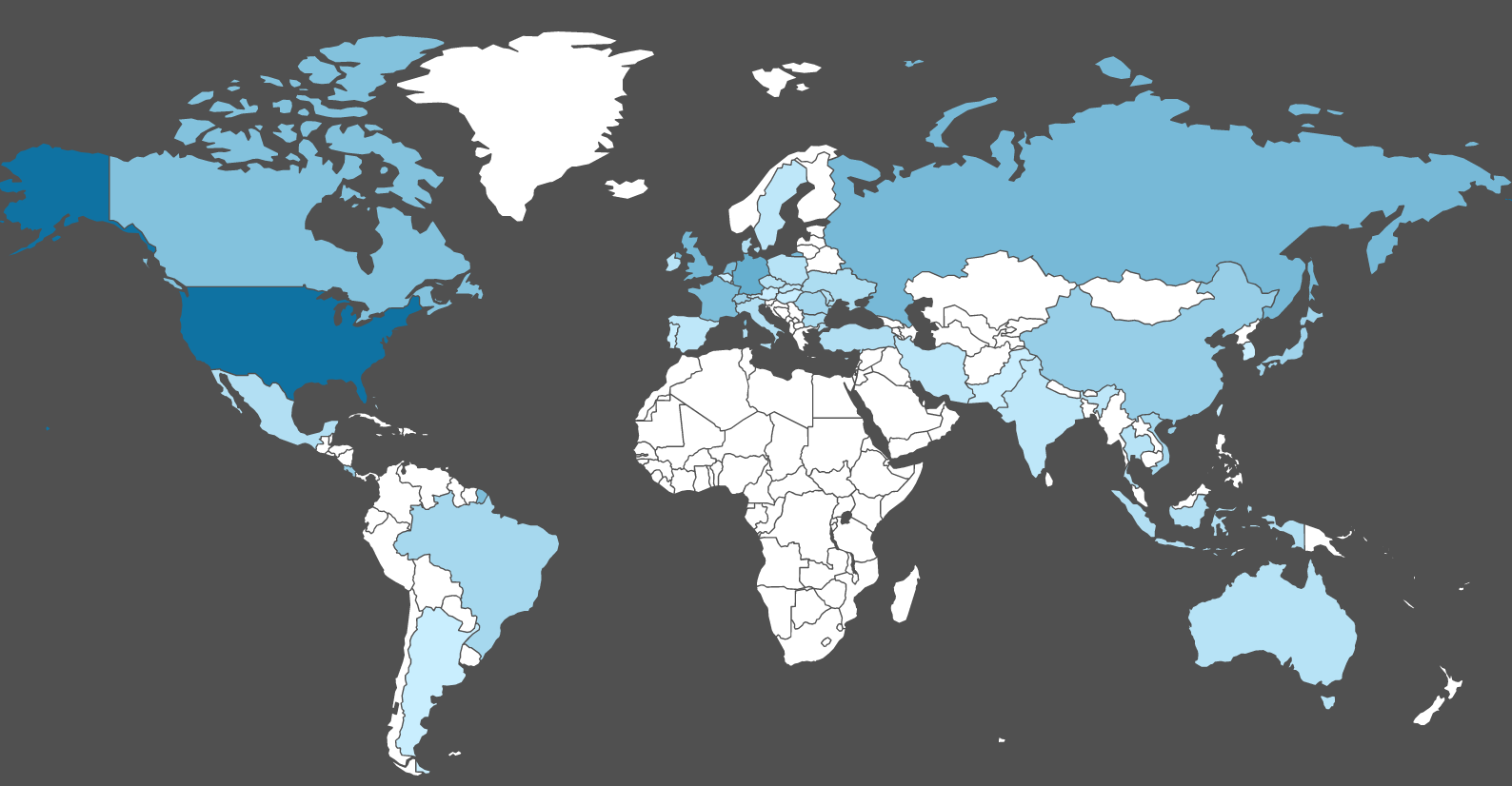
In addition, we analyzed the distribution of IPs to which these domains were resolved. We identified 1,172 IPs in total, located in 47 different countries with the majority being in US. Below is the figure showing the country-level distribution of these IPs.
Whois analysis
Through querying public Whois server as well as Domaintools, we obtained 861 valid whois records of 1,025 domains. We break the results down by registrant/emails and their registration dates.
Registrant/Emails: Not much can be learned due to the fact that most (521) are privacy protected by WhoisGuard. In the remaining registrants, there are also fake ones such as
AdministratorandPrivate Person. After removing the useless entries, we are only left with 80 different registrant, with no more than one registrant appearing more than 3 times. All the.biddomains are privacy protected. Since WhoisGuard service is not free (around $3/year), the.bidcampaign actors must be earning enough profit to offset this cost.Registration date: To better present details in registration date, we separate domains with different TLDs:
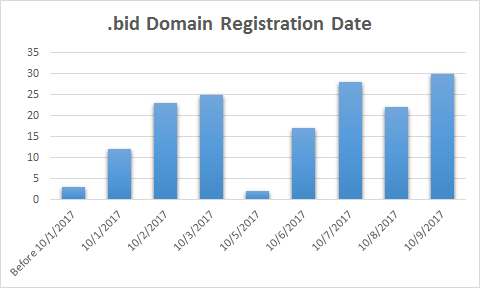
For .bid domains that we are able to retrieve whois information, most are registered after 10/01/2017 but spanning across multiple days, showing that the campaign is very recent and it has a rotating number of domains refreshing every day.
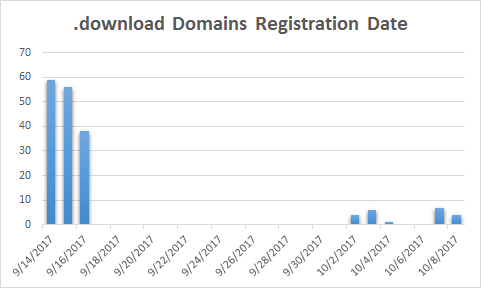
On the contrary, most .download domains were registered within 3 days of 09/14-09/16, 2017, with only a handful added on later. This looks to be a different campaign than the .bid ones. Similar registration trend can be found on .review domains (87 out of 103 are registered on the 3rd, 7th, and 8th of October 2017).
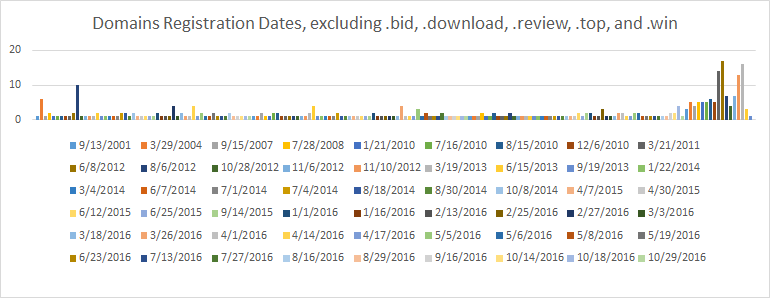
Finally, after we exclude the suspected campaign domains (.bid, .download, .review, .top, .win), the registration dates are extremely spreaded out from as early as 2001 to the current date. These domains are most likely either embracing the new crypto-mining monetization fever, or compromised by attackers to take advantage of their established reputation and high volume visitors.
5. Victim analysis
The URLs we crawled to detect crypto-miner presence comes from our PANDB cloud log. In this section, we analyze the demographics of visitors to such sites to shed some insights on their real-world impact.
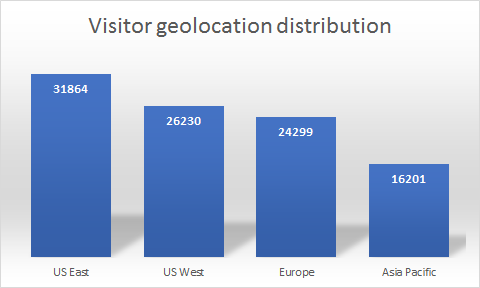
This figure shows the general geographic distribution of visitors to crypto-mining sites. While the US clearly dominates in total visiting counts, Europe and Asia Pacific is not too far behind. This graph indicates a broad spectrum of victims all across the globe.
After breaking down visits site-by-site, we found that the most visited sites more or less align with their Alexa ranking, with over 40K visits* to the 123moviews.co:
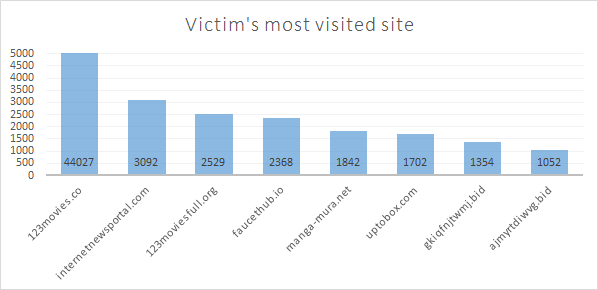
*: We only log a query when customer(s) using the same device visits the site for the first time in a TTL window. This does not count duplicate visits to the same site within a short timeframe. Therefore, the visits estimations are a lower bound.
6. Summary
As AdGuard has pointed out, the use of coinhive or similar mining services is itself not a malicious activity, it is how they are used that makes the sites malicious. Unfortunately, for the sites that we were able to observe crypto-mining activities, none of them has prompted the user with any sort of warning, let alone providing the kill switch for mining. To make matters worse, we have also seen malvertising and phishing being associated with unsolicited mining behavior. With Bitcoin soaring over $5K (at time of writing), we can only expect more of such services spawning from everywhere.
As a normal user, I recommend installing and enabling browser extensions such as Adblock or AdGuard, they have built-in detection of loading of such mining JavaScripts. Once detected, AdGuard will ask for user’s consent whether to block or run the script.