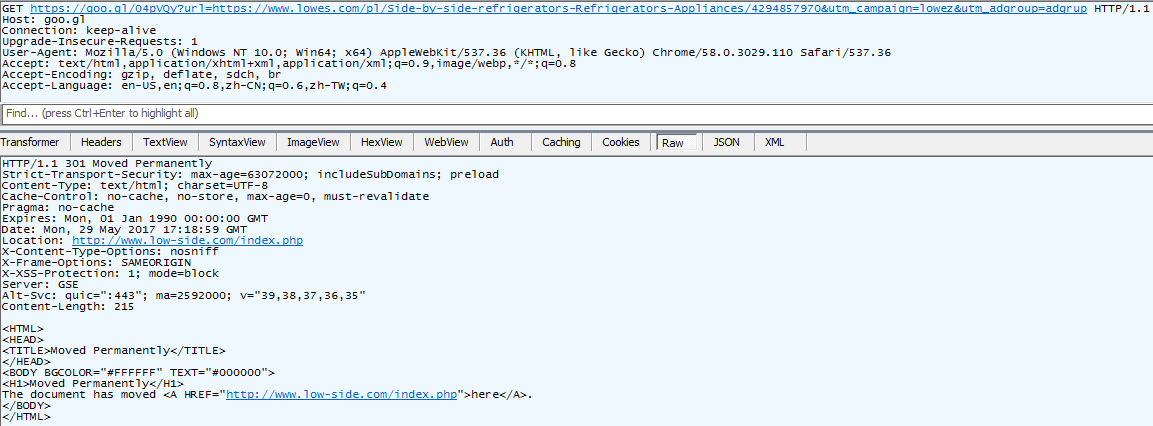
Apparently, Google (search result page) is not immune to malvertising!
Today, my wife came across a malvertising case directly from Google’s search result.
She was searching Lowes on Google, and search results showed something like this:
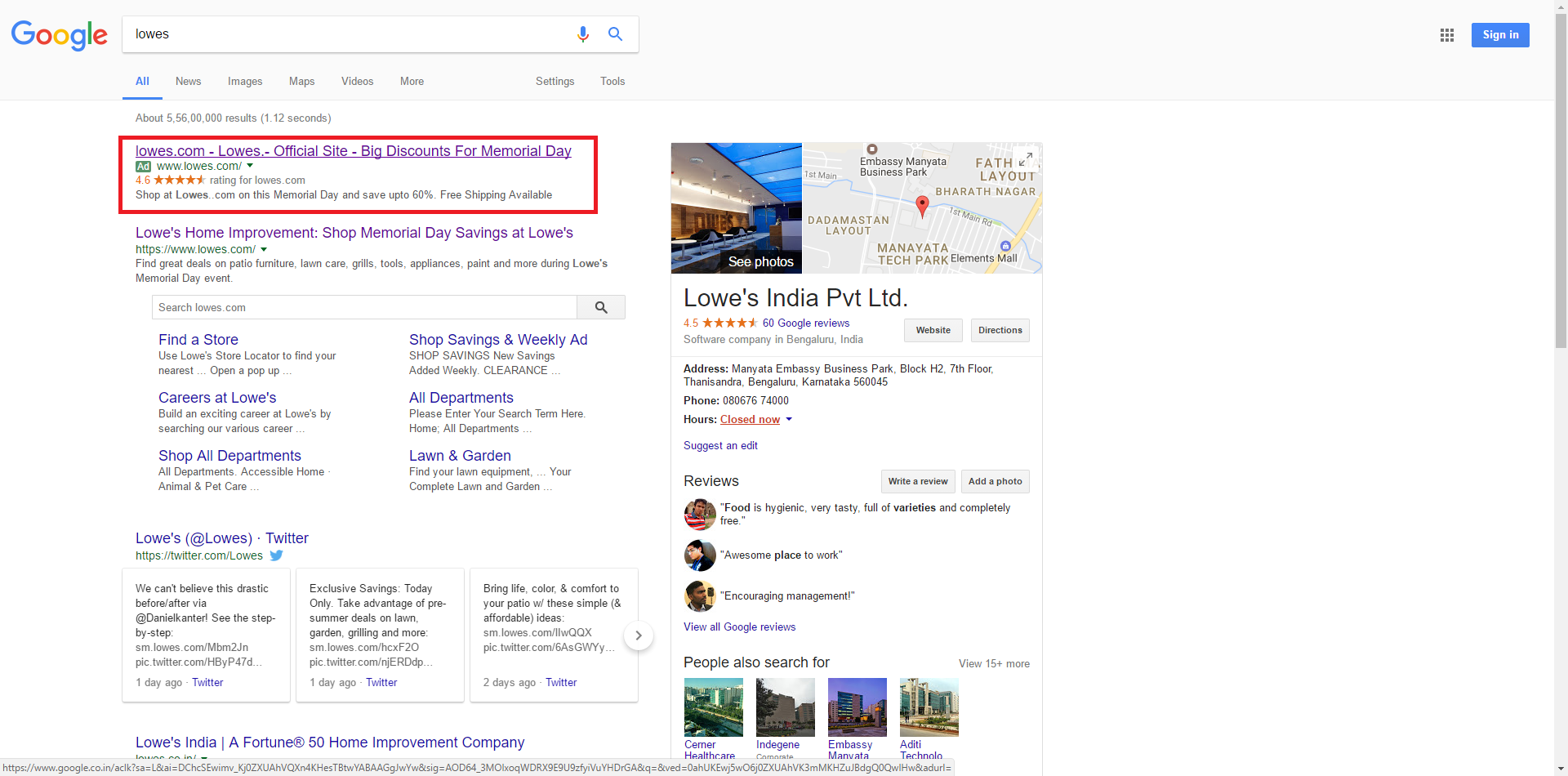
Without any hesitation, she clicked on the first link highlighted in the screenshot. This lead her to a page shown below:
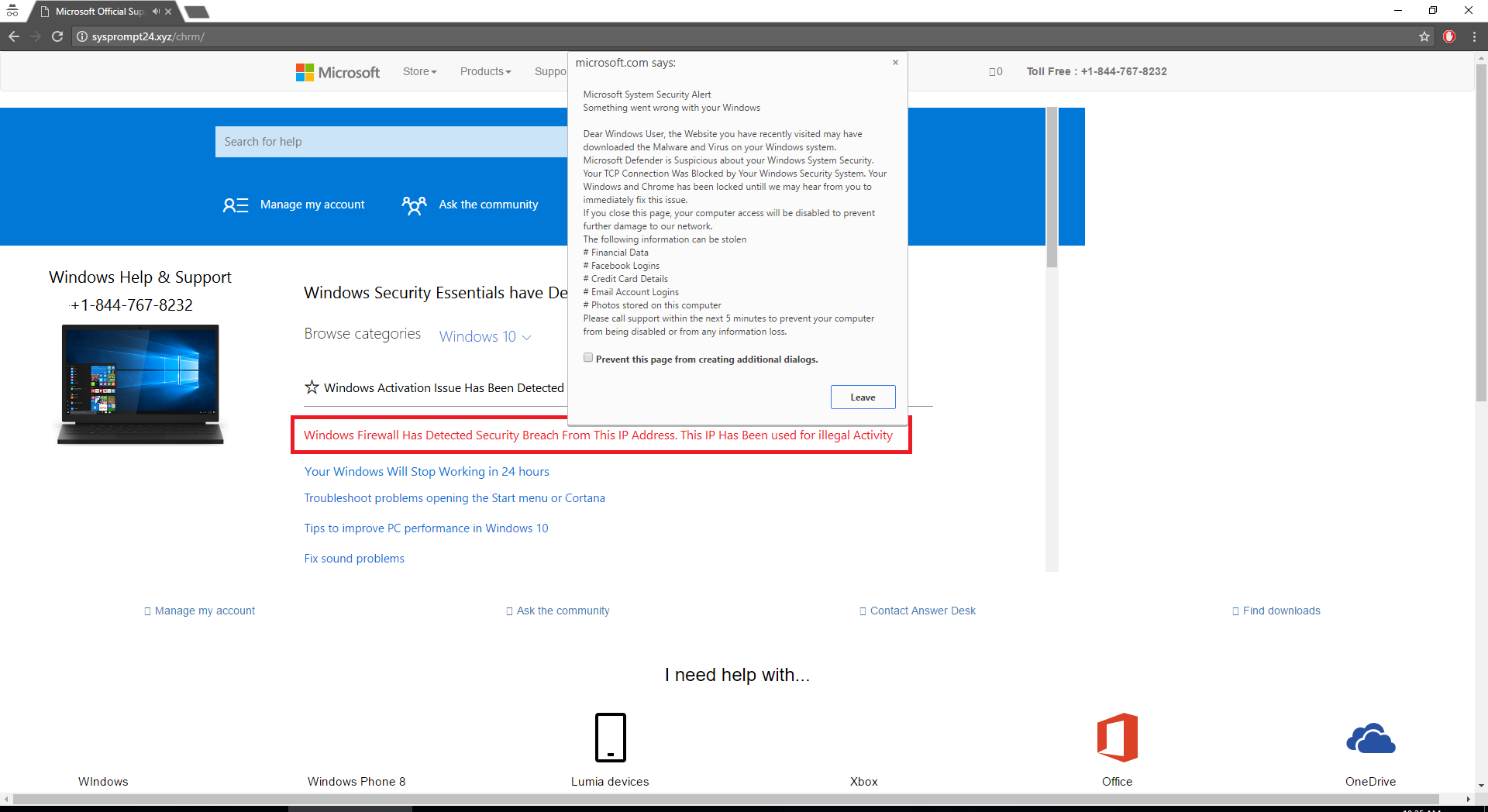
The attack maximizes victim’s screen and plays a warning message, indicating the victim’s machine has been compromised and request them to call the scam number. There is a recent comprehensive study about such scams in NDSS 2017 by Nick and his students.
Quite unbelievable. The first item in the search result has brought the user to a tech scam, claiming the victim’s computer has been infected with malware. Normally, a malvertising attack is hard to reproduce due to the randomness involved in the ad bidding process. However, I am able to consistently reproduce this attack on another machine, and I captured the traffic using Fiddler, shown below:
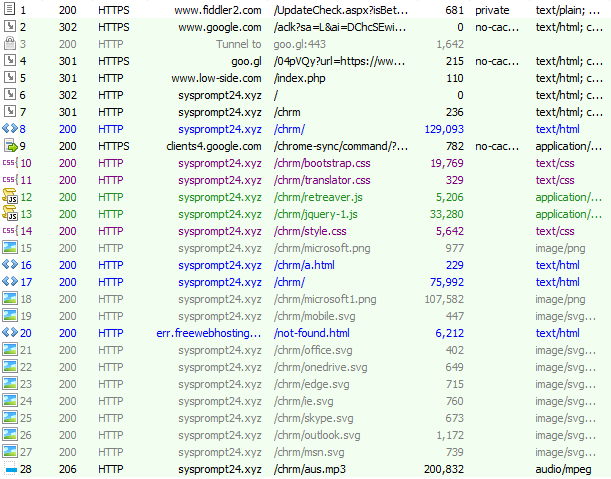
Picking the most interesting redirections in the chain:
You can clearly see that goo.gl 301ed to a rogue domain, named www.low-side[.]com.
From there, all hell breaks loose.
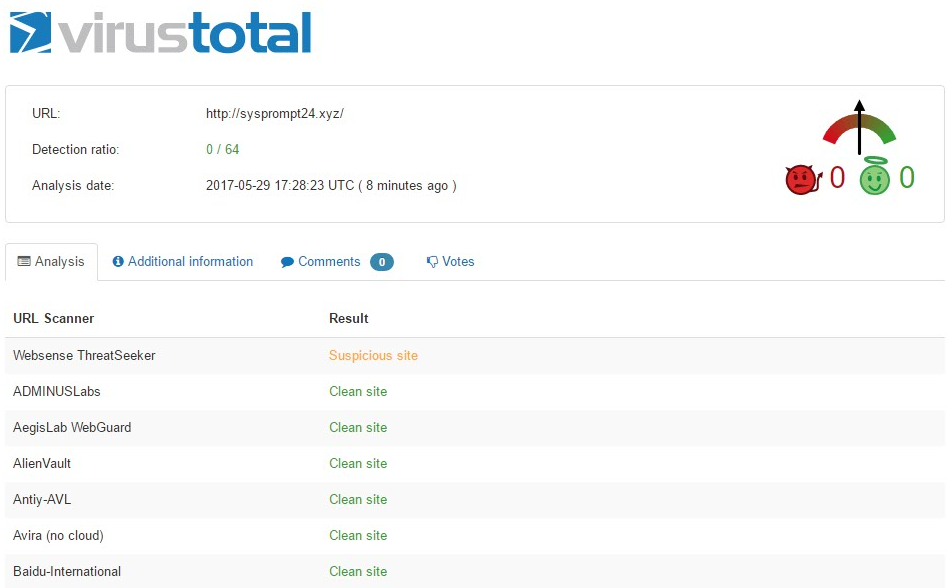
VirusTotal on this domain (at the time when malvertising is working):
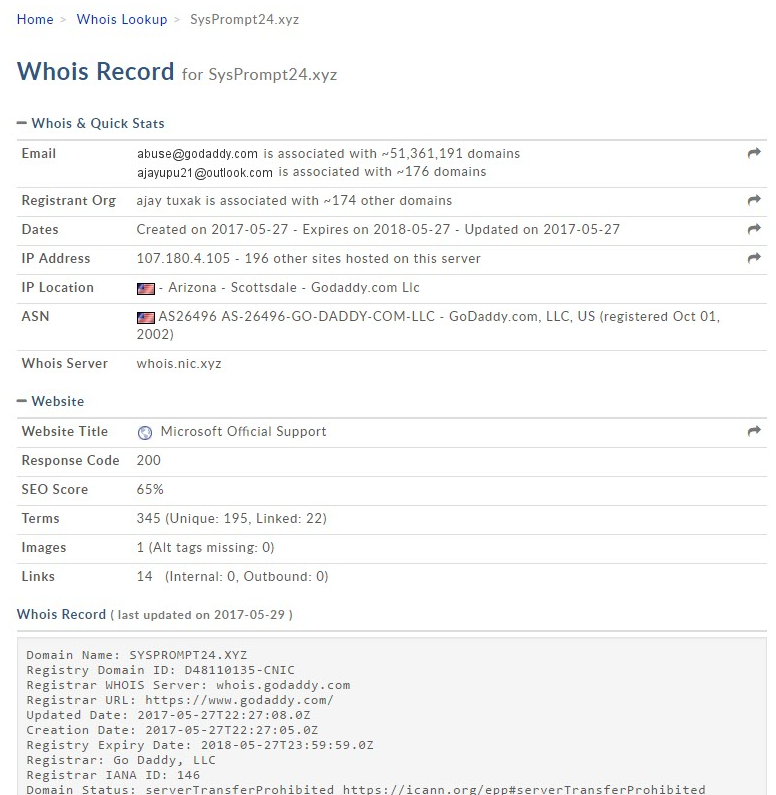
Whois information on final domain serving tech scam content:
Google was able to take down this malvertising roughly after 30 minutes since my wife came across it. However, we never knew when the attack initially started. Several takeaways I got from this:
- We can’t take things for granted - even Google is subject to malvertising attacks in their promoted search results.
- While Google is (for most cases) fast to respond to attacks, threat prevention still offers much more than detection, and should be the holy grail everybody is chasing. To this end, we still have a ways to go.